Contract Cybersecurity: What are the Risks?
According to the Identity Theft Resource Center, the number of data breaches reported so far in 2021 has already exceeded last year’s total, putting this year on track for a record number of cyberattacks. Malicious actors are attacking and stealing all types of data, including the valuable data contained in your organization’s contracts.
To protect your contract data, you need to enhance your organization’s cybersecurity efforts. Read on to learn more.
Key Takeaways
- Cyberattacks and data breaches are increasingly costly.
- Contracts contain some of your most sensitive data that is very valuable to cybercriminals.
- To strengthen cybersecurity for your contracts, require strong user authentication, keep hardware and software updated, centralize your contract storage, and restrict contract access.
- Contract lifecycle management software significantly improves contract cybersecurity.
Cyberattacks Are on the Rise: Statistics
The facts are clear: cyberattacks are increasing. Here are some of the latest statistics you should know:
- Last year, AV-TEST research institute discovered more than 137 million new malware samples.
- According to CyberEdge’s Cyberthreat Defense Report, a record 86.2% of all organizations are expected to experience cyberattacks in 2021, up from 80.7% in the previous year.
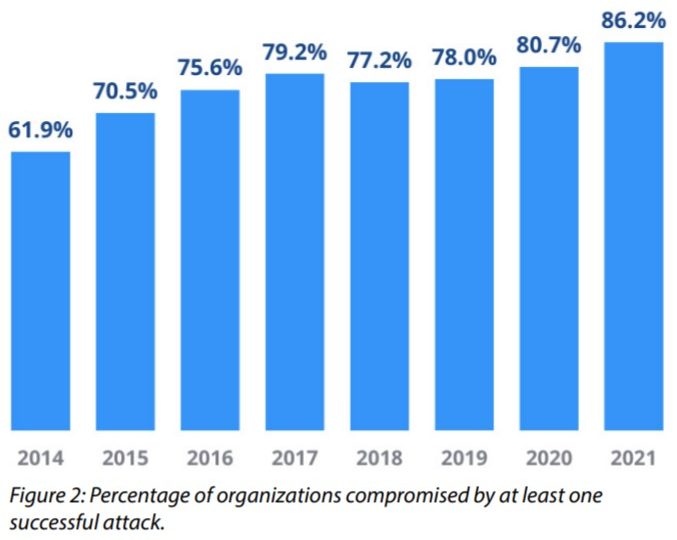
SOURCE: Cyber Edge
- According to the IBM X-Force Threat Intelligence Index, ransomware was the number-one type of cyberattack in 2020.
- Ransomware attacks are also on the rise, nearly doubling in the first half of 2021 according to the Cognyte CTI Research Group.
The following video details the biggest data breaches of 2020.
SOURCE: Solutions Review via YouTube
Cyberattacks Are Costly: Statistics
Cyberattacks are not only increasing – they’re becoming increasingly more costly.
- Forbes reports that every single minute, enterprises lose $2,900,000 to cyberattacks.
- According to IBM, the average cost of a data breach is $3.86 million, although that number varies by industry. The total cost of a data breach includes detection and recovery costs, ransomware payments, downtime costs, the cost of lost customers, and the cost to companies’ reputations.
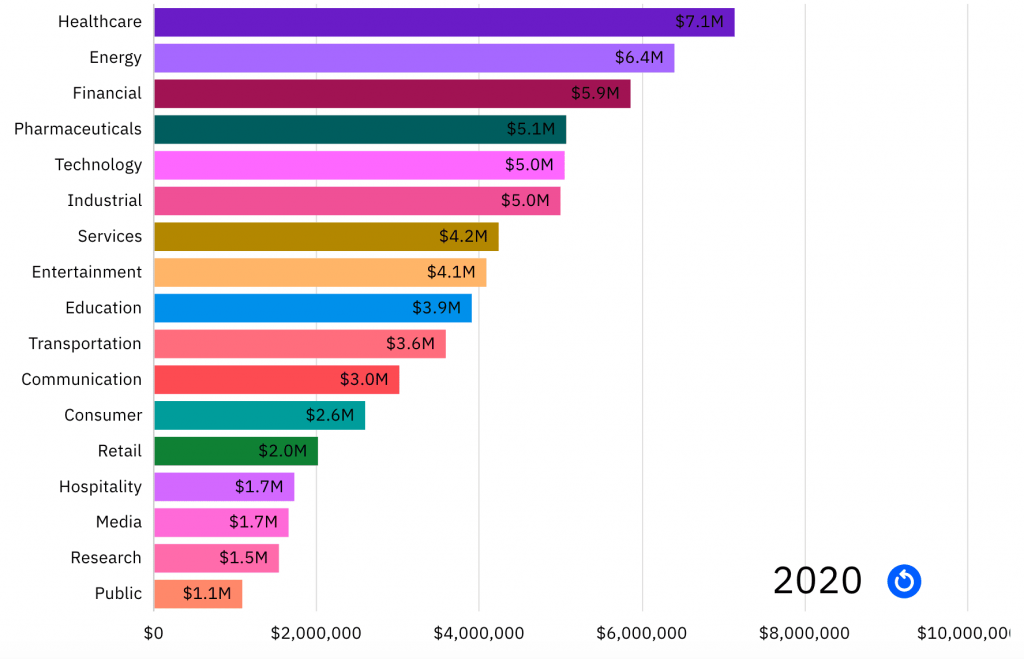
SOURCE: Digital Guardian
- If a ransomware attack hits your organization, know that ransom demands can vary. While the most common ransom demand is $10,000, demands in 2020 went as high as $3.2 million.
- According to the Sophos State of Ransomware 2021 Report, the average ransomware demand in 2020 was $170,404.
Your Contracts Contain Valuable Data of Interest to Cyberattackers
What does all this data about cyberattacks have to do with your organization’s contracts? The answer is: Plenty.
Cybercriminals attack organizations to get their data. Some malicious actors want to steal confidential customer information and sell it on the dark web. Others want to steal valuable trade secrets. Ransomware attackers want to hold valuable data hostage in return for a hefty ransom payment. Still, other bad actors just want to create havoc by deleting important files.
In other words, cyberattacks are all about the data – and your contracts contain a wealth of confidential data. Cyberthieves want access to your contracts to obtain:
- Client/supplier names and personal contact information
- Confidential information about your company
- Legal details
- Financial data
- Bank account information
- And more
Every contract you execute contains this type of confidential information. Any malicious party accessing your contracts can sell this information to the highest bidder. This can cause untold issues for your company, your customers and suppliers, your partners, and even your employees. A data breach affecting your contract data can even put your organization at risk for noncompliance with industry and governmental privacy regulations, subjecting you to substantial fines and even legal action.
How Your Contract Data Can Be Breached
How can cyberattackers breach your confidential contract data? Cyberattacks result from the following causes:
- Phishing, spear phishing, and other social engineering techniques
- Human error
- Weak or stolen passwords
- Malware
- Backdoors and other system vulnerabilities
- Too many permissions
- Unencrypted data
- Insider threats (disgruntled current or former employees)
These risks increase when contract management in an organization is lax. For example, contract data is at risk when contracts circulate throughout your firm for approvals and signatures without proper security. The contract risk increases when contracts are located in multiple departments and locations throughout your organization, instead of being stored in a central secure location.
How to Strengthen Contract Cybersecurity
The valuable data contained in your organization’s contract is an attractive target for cybercriminals. To protect your contract data, you need to strengthen your firm’s contract cybersecurity in contract management. You can do this in the following ways:
Require and Enforce a Strong User Authentication Policy
Many people use short or easily guessable passwords, even for their business accounts. You need to require your employees to use strong passwords (i.e., passwords that contain a minimum number of characters with a mix of numbers, symbols, and lower and uppercase letters) on all accounts and devices – and to change them regularly. To enhance password security, employ multi-factor authentication and single-sign on technologies.
Contract management software from Contract Logix employs robust user authentication capabilities including authentication types, password policy configuration, and session settings for time-outs after a certain number of failed attempts Read this blog on How to Leverage CLM Authentication for Increased Security and Compliance to learn more.
Regularly Update All Software and Hardware
One way that malicious actors gain unauthorized access is by exploiting security holes in both software and hardware. The best way to guard against these opportunistic attacks is to make sure that all software and connected devices are regularly updated with the latest security patches and upgrades.
Since Contract Logix is a cloud-based contract lifecycle management solution hosted on the ultra-secure Microsoft Azure, you can rest assured that the software will always be using with the latest security updates.
Centralize Contract Storage
Contracts that are spread out across your entire organization present unnecessary targets for cybercriminals and even run the risk of getting lost or misplaced. Instead, store all your contracts in a single secure location, in the cloud. Using a centralized contract management repository like Contract Logix ensures all of your contracts are housed in one secure cloud-based destination. This also makes all of your contract data easy to locate, search, analyze, and report on which can deliver the business additional insights.
Employ Data Encryption
When data is encrypted, only users with the proper decryption key can read it. Any unauthorized user trying to access encrypted data sees only gibberish. For this reason, all of your stored contracts – as well as contracts in process – should be encrypted.
Contract Logix encrypts all your contract data at rest and in transit using the latest encryption technologies such as AES 256 and TLS 1.2. All your contracts and related information is automatically encrypted in case a hacker tries to steal or intercept it.
Restrict Access
Not everyone in your organization needs access to all your contracts. Instead, limit who has access to specific contracts via the use of least privilege access, which grants employees access only to those contracts essential to performing their assigned duties.
Contract management software from Contract Logix supports robust yet easy-to-configure role-based and feature-based permissions. You can easily determine what roles have access to what information in the software. This not only ensures appropriate access and security, it also improves the user experience by only showing them relevant information.
Embrace Contract Lifecycle Management
Perhaps the best way to minimize contract cybersecurity risks is to use contract lifecycle management (CLM) software. A robust CLM platform, such as the one offered by Contract Logix, not only protects your contract data but also automates much of the contract workflow. It’s also import that your contract management platform supports the latest security standards and certifications including SOC 2 Type II, HIPAA, FISMA, and PCI compliance.
Let Contract Logix Help Improve Your Contract Cybersecurity
When you want to improve the cybersecurity for your organization’s important contracts, turn to the experts at Contract Logix. Our CLM solutions automate the entire contract lifecycle and centralize the storage of all your contract data, all of which reduce the risk of data breach. You’ll also realize the benefits of streamlined workflow, improved accuracy, and lower costs.
Contact Contract Logix today to learn more about improving contract cybersecurity for your organization.


