Smart Contract security in 2023: A Simple Checklist
Dec 14th, 2022
What are smart contracts—and how secure are they? Blockchain technology makes smart contracts possible but introduces security issues not present with traditional contracts. If you want to employ smart contracts in your organization, work through a detailed smart contract security checklist, and prepare yourself for a different set of challenges than you’re currently used to.
Key Takeaways
- Smart contracts are enabled by blockchain chain technology and automate contract execution and fulfillment
- Security vulnerabilities in smart contracts have resulted in more than $4.75 billion in financial losses since 2012
- A smart contract security checklist includes following best practices, limiting access to key functions, minimizing code complexity, testing and auditing contract code, and developing a disaster recovery plan
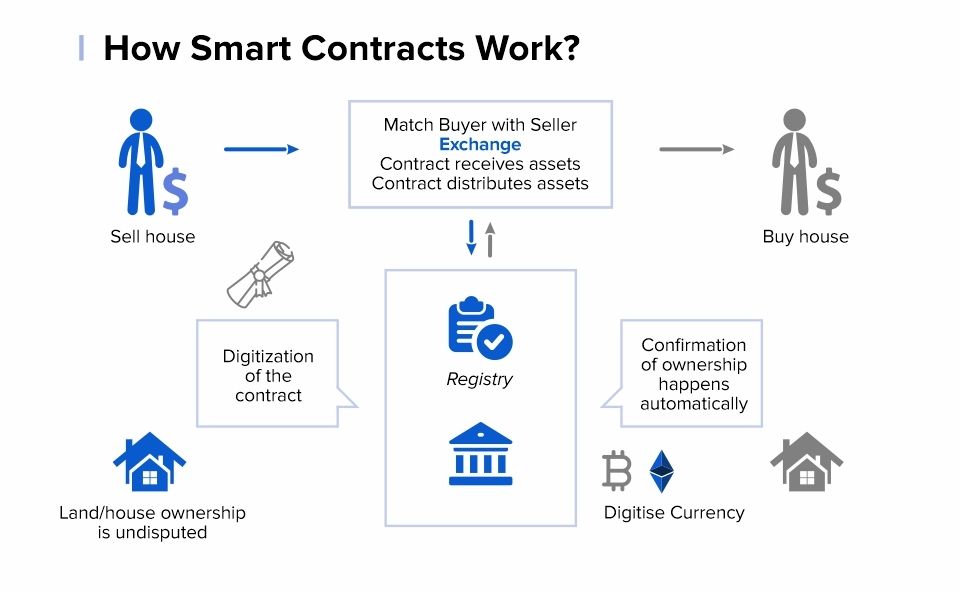
What Is a Smart Contract?
 SOURCE: https://2muchcoffee.com/
SOURCE: https://2muchcoffee.com/
A smart contract is part of blockchain technology—the same technology behind Bitcoin and other cryptocurrencies. Smart contracts consist of digitized terms and conditions of crypto-based transactions. They’re nothing more than lines of code that specify the terms of the agreement between two parties. A smart contract remains coded for a decentralized blockchain network, so central authority does not regulate it and is not subject to any legal system’s laws and regulations.
Unlike traditional contracts, the terms of a smart contract automatically execute when specified conditions arise. Smart contracts cannot be altered, tampered with, or deleted and are not subject to human interaction or error. All interactions with smart contracts are irreversible.
How Secure Are Smart Contracts?
Smart contracts are a high-tech solution to traditional contract management problems. Because terms execute automatically and the underlying code isn’t alterable, many blockchain enthusiasts gravitate toward smart contracts.
Unfortunately, blockchain technology is not bulletproof. As recent news reports have shown, there is ample opportunity for fraud with blockchains and cryptocurrency, with zero legal and governmental protection afforded. Because all blockchain transactions are anonymous, stolen assets are almost impossible to track down, and resulting losses are typically irrecoverable.
Over the past decade, some sources put the losses due to poor smart contract security at $4.75 billion. Recent high-profile incidents, such as Ronin’s $615 million breach and Wormhole’s $326 million signature verification hack, have made users justifiably wary of trusting their financial assets to smart contracts.
A Checklist for Smart Contract Security
Individuals or organizations desiring to employ smart contracts must take all necessary security precautions to protect their financial assets. As a start, work through the eight items on this smart contact security checklist.
Follow Best Practices
The first thing you should do when developing a smart contract is to follow all development and blockchain best practices. These might not be obvious to contract professionals, but developers should be aware of them. These best practices include:
- Employ a secure development environment for coding, testing, and deploying all smart contracts
- Store all code in a secure version control system
- Make all code modifications via pull requests—and ensure that all pull requests have at least one independent reviewer
- Verify that all code compiles without errors
- Thoroughly document all contract code
Limit Access to Key Functions
Many smart contract functions are marked public so external accounts can interact with them. Unfortunately, giving widespread public access to smart contract functions opens the door to malicious actors. A better approach is limiting access to key functions, so authorized accounts can only access them. This sort of role-based access control is an effective way to prevent unauthorized users from accessing secure data.
Use Appropriate Function Statements
Smart contracts consist of many lines of code, with each line representing a distinct function. Security improves when using function statements to guard against complex contract operations. In particular, you can use the following statements to revert to identify unapproved changes and revert the smart contract code to a previous state:
- require()
- assert()
- revert()
Minimize Code Complexity
The more complex any piece of code, the more likely it is to contain errors or vulnerabilities. Keep your smart contract code as simple as possible. Reuse trusted existing libraries when you can and split common business logic across multiple contracts.
Test the Code
Don’t assume that a smart contract will work as designed. Always test your smart contract code to confirm that it meets quality standards and doesn’t produce any unexpected results. It’s best to test your code in small batches before the contract finalizes.
Conduct an Independent Code Review
For added security, commission an independent review of your smart contract code. Use a third party to validate the code and look for potential flaws. You can also set up a “bug bounty” program to encourage whitehat hackers to find vulnerabilities in your contract code.
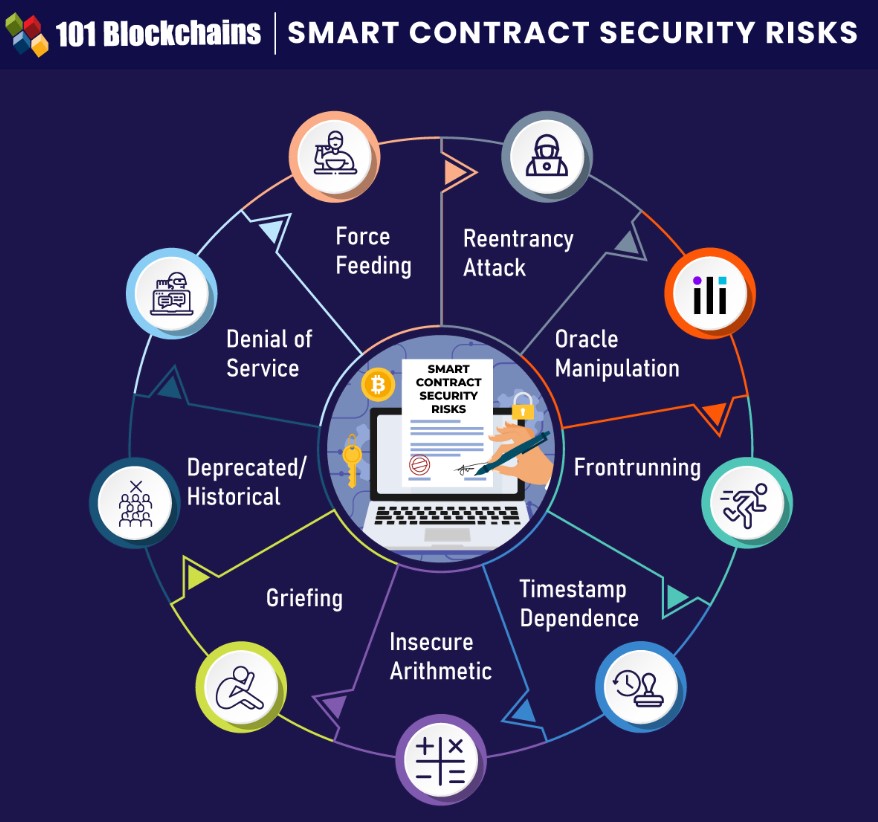
Guard Against Common Vulnerabilities
There are several common smart contract vulnerabilities that you should actively defend against. These include:
- Reentrancy attacks
- Oracle manipulation
- Frontrunning
- Timestamp dependence
- Insecure arithmetic
- Griefing
- Deprecated/historical vulnerabilities
- Denial of service (DOS) attacks
- Force-feeding
Guarding against these vulnerabilities requires the proper technical training and tools. A smart contract security kit includes visualization, classification, static and dynamic analysis, and testing tools. It’s also helpful to conduct periodic audits of your smart contract security with these particular risks in mind.
 SOURCE: https://101blockchains.com/
SOURCE: https://101blockchains.com/
Develop a Disaster Recovery Plan
What do you do if a smart contract is breached? The last item on the smart contract security checklist is to develop a disaster recovery plan, just in case the worst happens.
A robust disaster recovery plan should include the following elements:
- Event monitoring. By monitoring contract events, you can track calls to contract functions and monitor any changes to key variables. This overview lets you know when another party engages in a critical action, such as withdrawing funds and lets you discover any malicious actions more quickly. With proper monitoring, you can respond faster to any breaches and hacks and take the necessary action to fix the problem and mitigate its impact.
- Emergency stops. If an unauthorized event occurs or you discover vulnerabilities in your code, you must patch the faulty code. Unfortunately, you can’t do this when the code is running. As part of your disaster recovery plan, you need to be able to enact an emergency stop that blocks all calls to vulnerable contract functions. These contract functions let you change the code in question and deal with any issues that have arisen.
- Contract upgrades. While blockchain contracts theoretically can’t be altered, you can include upgrade patterns in the code to correct any critical flaws you discover. Upgrading often occurs with so-called proxy patterns, which utilize two separate contracts. Accounts interact with a proxy contract, which references a separate logic contract. Upgrades happen when deploying a new logic contract without modifying the code of the proxy contract.
For Ultimate Contract Security, Use Contract Logix’s Contract Lifecycle Management Solution
Even if you work through all the steps in the smart contract security checklist, smart contracts are still considerably less secure than traditional contracts—especially when those traditional contracts are managed through an advanced contract lifecycle management (CLM) system. Contract Logix’s CLM solution automates the traditional contract cycle from initiation and negotiation through execution and fulfillment. It’s a secure solution not subject to the vagaries of blockchain technology.
Contact Contract Logix to learn more about secure contract management.
Looking for more articles about Contract Management? Check out our previous article “How Legal Ops is Driving Digital Transformation in 2023“.
Accelerate Your Digital Transformation With Contract Logix
Download our Data Extraction Product Brief to learn how you can automate the hard work using artificial intelligence


