Information Security Management for Contracts & Documentation
In 2021, incident reports of data breaches involving the public exposure of sensitive private information rose 68%, capping the highest year-over increase on record. The spike in data breaches fits into a generalized surge in cybercrime – up 600% – since the shift to remote work that began in the early months of the COVID-19 pandemic in 2020. Set against the backdrop of an ongoing IT labor shortage of half a million jobs, companies face a complex, evolving set of challenges for information security management (ISM) in 2022.
For most infosec experts, the escalation of attacks on sensitive business data admits a relatively simple explanation. Starting in the spring of 2020, companies rapidly accelerated digital transformation plans, migrating workloads en masse to cloud storage hosts and various software-as-a-service (SaaS) providers. As of Q1 2022, 56% of businesses had moved more than half their workloads to the cloud, and nearly 99% reported adopting at least one SaaS platform in their day-to-day operations. During these adaptations, businesses effectively connected terabytes of new sensitive data to remote access points for the first time.
Companies now face more breaches and attacks involving private data because they have created more vulnerabilities and targets than ever.
For companies with valuable digital assets to protect, the pressures of digital adaptation vie with mounting risks of breaches and intrusions, creating an environment of uncertainty regarding ISM best practices. In this guide, you’ll learn what ISM is and how it applies to the handling and protection of digital assets such as contracts and other forms of sensitive documentation.
Key Takeaways
- Recent developments in the IT security landscape have made information security management (ISM) a high priority for businesses across industries.
- ISM involves identifying risks to information in an organization and implementing practices and technologies that mitigate those risks according to probability and severity.
- Certain ISM best practices for securing contracts and documents apply broadly in most business contexts.
SOURCE: Jon Good via Youtube
What Is Information Security Management?
Information security management (ISM) refers to the tools and practices organizations employ to protect their data from vulnerabilities and external threats. The chief responsibility of information security professionals is risk mitigation. ISM professionals accomplish risk mitigation in a two-step process.
- Identifying and qualitatively assessing the set of information security risks that apply to an organization
- Putting in place practices and technologies that address those risks according to their known likelihood and severity
Risk identification and assessment require understanding how an organization stores and transmits information. In the case of storage, organizations may use owned onsite servers, cloud storage services, or a hybrid plan of both. Regarding transmission, information users within an organization may exchange potentially sensitive materials by minimally secure means such as hard copies and email, highly secure end-to-end encrypted channels, and – more often than not – some ad hoc combination of both. In applications to particular organizations, ISM systems should begin with two questions.
What Information Security Risks Apply?
Some storage architectures and transmission protocols eliminate certain information security risks. For example, strictly onsite facilities do not need to worry about malicious insiders selling user credentials anonymously online to buyers who would not be able to access the physical location of systems. Likewise, administrators of wholly cloud-based systems do not need to consider the risk of catastrophic data loss associated with destroying a physical facility in a natural disaster such as a fire or earthquake.
What Is the Likelihood of Applicable Risks?
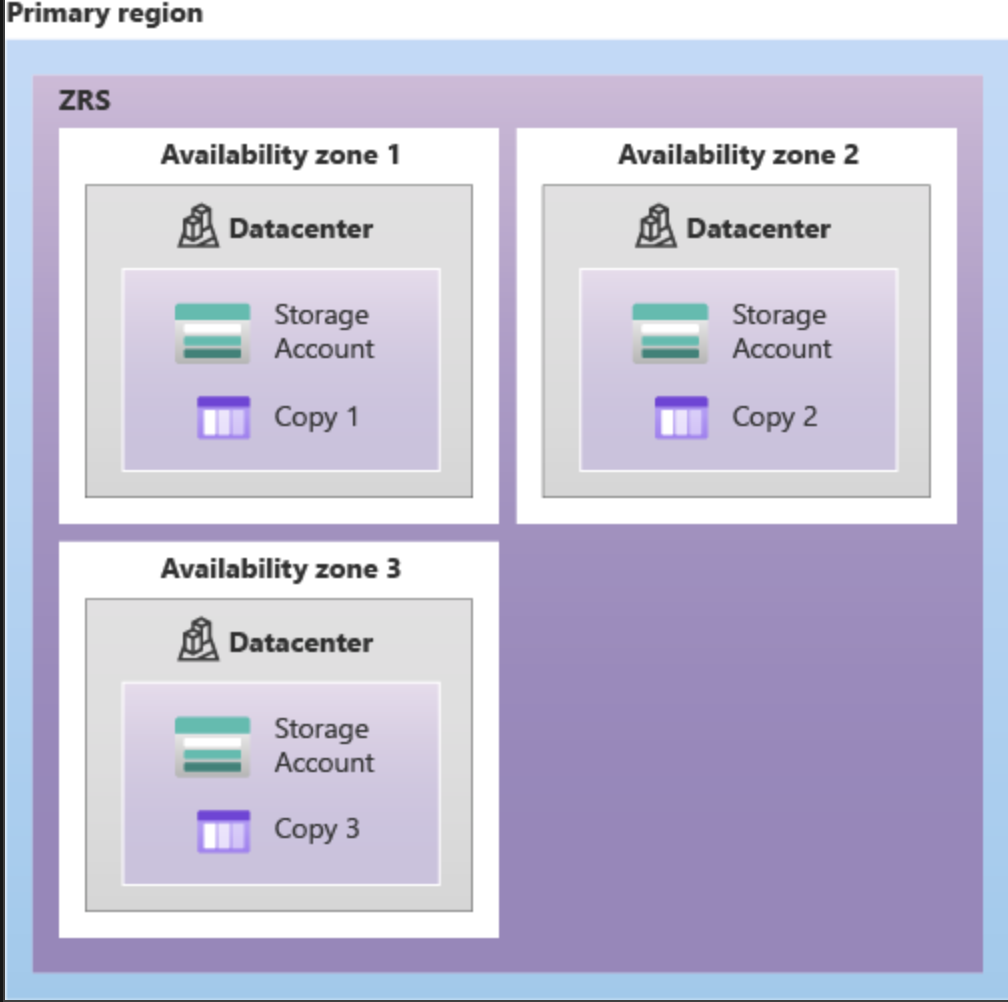 Image Source: https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy
Image Source: https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy
The design of some systems may render certain information security risks technically possible but of such infinitesimally low probability that ISM strategies should disregard them. For example, cloud storage providers replicate multiple data instances to mitigate the risk of loss by destroying hardware. In arrangements such as those provided by Microsoft’s Azure or Amazon Web Services, clients choose from two tiers of redundancy that either replicate data on three separate hardwares in the same facility or in physically disparate facilities in a specified zone. The first option guarantees data persistence with a net vulnerability equal to 1 in 1 billion per year, while zone-based redundancy reduces the chance to 1 in 1 trillion per year.
Thus, effective ISM strategies will focus on risks with non-negligible likelihood and prioritize those occurring with the highest frequency. For instance, cloud-based IT systems – particularly multi-cloud – are notoriously vulnerable to insider threats. In all system architectures, human activity accounts for 88% of data breaches. Of these, 40% involve deliberate criminal intent by insiders who sell or leak privileged credentials capable of breaching secure systems.
 Image Source: https://www.code42.com/glossary/what-is-insider-threat/
Image Source: https://www.code42.com/glossary/what-is-insider-threat/
3 ISM Practices and Technologies for Securing Contract and Document Data
Implementing ISM practices and technologies to mitigate the severe, high-frequency risks associated with a particular organization depends on the kind of information you need to protect. Variables, in this case, would include whether the system circulates information widely within an organization or restricts access to a limited number of authenticated users. Also relevant would be the frequency of transmission to third parties outside the organization.
To make an example of ISM in the context of contracts and sensitive documentation – content that may vary broadly in either direction for a breadth of access and frequency of transmission – certain information handling practices and secure technologies apply broadly. Here are three that belong in any ISM strategy.
- Establish a Single Secure Repository
In risk assessment, every instance of a vulnerability causes the probability of failure to be multiplied. Storing all sensitive content such as contracts and related legal documents in a single repository reduces the chances of unauthorized ingress radically. It’s critical to use contract management software that’s hosted with a secure and reliable provider such as Microsoft Azure. You will also want to make sure access to the repository has the appropriate authentication and permission settings which leads us to the next item.
- Implement Multi-Tier Least Privilege Authorizations
Cloud-based contract management providers now offer advanced user provisioning as a standard service. Organizations should leverage this capacity on the principle of least privilege to minimize unnecessary user access to sensitive information. For starters, you will want to ensure you can set up the right level of role-based and feature based permissions. Second, you will want to establish the proper authentication settings such as password lengths, character types, timeframes for lock out, and more. Finally, leverage single sign-on and multi-factor authentication integrations and capabilities.
- Use Exclusively Encryption-Secured Portals for Document Transmission
The best security technologies on the market can’t account for how well or poorly users and clients may protect their email credentials. Strong ISM policies will only allow users to exchange sensitive information via encrypted services, preferably SOC 2 Type 2 verified. Since you will be uploading and downloading information from the repository it’s also important that it encrypts your data both at rest and in-transit using the latest encryption technologies.
Contract Management Solutions with Contract Logix
Trusted by thousands of legal, procurement, and finance professionals across various industries, Contract Logix’s contract management platform streamlines your contract lifecycle with a suite of information security management features. It is an incredibly secure and reliable platform that is SOC 2 Type II, HIPAA and FISMA compliant and supports a security-first approach to contract management with encryption, role-based and feature-based permissions, MFA, SSO, and many other capabilities.
To request a live demo and learn more, contact Contract Logix today.
Looking for more articles about Contract Management? Check out our previous article “Importance of Improving Contract Management for Healthcare Providers“.


