How to Ensure Data Protection with the Contract Compliance Process
Contract compliance is essential for effective contract management. The contract compliance process, however, can put your valuable contract data at risk. Do you know how to protect your data during the contract compliance process? There are a number of things you can and should do to ensure robust data security.
Key Takeaways
- The data compliance process ensures that your contracts comply with company standards and government regulations such as GDPR and HIPAA, as well as that all contract terms are complied with
- An audit of your contracts for compliance purposes can put your data at risk
- To ensure data protection during the contract compliance process, make sure your auditors are working with digital files from a central contract repository, and that they have restricted, password-protected access to all files
- In addition, you need to establish a detailed audit trail, encrypt all files and communications, and deploy contract lifecycle management software
What is the Contract Compliance Process?
The contract compliance process reviews existing contracts to determine:
- If the contract complies with company standards
- If the contract complies with government and industry regulations
- If the contract terms have been complied with by both parties
The process is essentially similar to that of a contract audit. A designated individual or team examines a selection of contracts to verify each contract’s compliance, identifying areas of noncompliance. Contracts that do not meet the necessary standards are pulled out so that issues can be rectified.
Rectification can include:
- Rebilling any unfulfilled payments from the other party
- Fulfilling any late deliverables or payments
- Renegotiating nonstandard or unreasonable terms
- Ensuring compliance with all necessary regulations, even if not stipulated in the contract
Protecting Contract Data During Compliance
The contract compliance process involves retrieving, analyzing, and otherwise working with a large quantity of data. This includes the contracts themselves as well as supporting documents, invoices, financial records, receipts, and more. During the compliance process this data is vulnerable to unauthorized access, loss or misplacement, or theft. For this reason, it is imperative that all contracts and related data be protected during the contract compliance process.
Contract security during the compliance process employs many of the same security processes used to protect your contracts during the normal contract workflow and ongoing post-execution management. It’s all about keeping your data out of the hands of unauthorized users.
Work with Digital Files
It’s easier both to work with and secure your data if it is all in digital format. Working with physical contracts and supporting documents is time consuming and messy. It’s easy for a paper contract to get misplaced or even stolen. Digital contracts are easier to access, easier to share among team members (especially those in remote locations), and easier to secure.
If your organization has yet to embrace digital contract management, now is the time to do so. This involves digitizing all previous paper contracts and starting all new contracts electronically. You should also digitize all supporting documents.
Audit from a Central Contract Repository
When your contracts are all digital, it’s easy to access and audit them directly from where they’re stored. Ideally, this is a central digital contract repository; contract management and auditing is made more difficult when contracts are located in different departments and locations within your organization.
With a centralized contract repository, such as one created with a contract lifecycle management (CLM) solution like Contract Logix, auditors can access all current and archived contracts electronically. No contracts need to be physically retrieved or temporarily relocated to the auditor’s location. Auditors can access all necessary files from wherever they’re located, via the Internet.
Restrict Access
Most archived contracts should have severely restricted access. This access can be expanded to include members of the compliance audit team – but only authorized individuals. This should comply with your organization’s existing role-based permissions policies. You may even want to restrict auditors to read-only access, so they won’t be able to edit contracts without additional permission. With contract management software, you can configure role-based and feature-based permissions to very effectively, easily, and granularly regulate who has access to what information.
Require Strong Passwords
Access to stored contracts should be password protected, even to those auditing the process. Unfortunately, many people create short or easily guessable passwords. For your purposes, require employees to create strong passwords – and to change those passwords on a regular basis. Contract management software makes if very easy to ensure all passwords follow your IT security policy requirements in terms of length, use of special characters, frequency of update, etc.
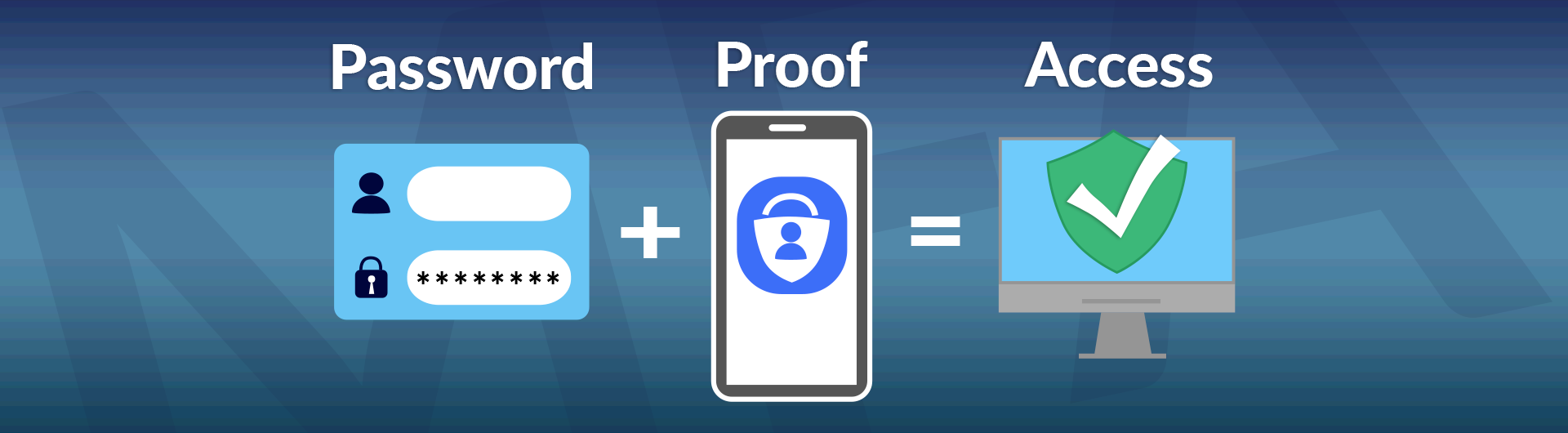
Employ Multi-factor Authentication
Password security is significantly enhanced when you employ multifactor authentication (MFA). MFA adds a second method of authentication after the user has entered their password, typically a separated code that is emailed or texted to the user. Experts say that adding MFA to your existing password security can reduce unauthorized access by 80%-90%. Some contract management software solutions like Contract Logix make it very easy to activate MFA.
 SOURCE: csulb.edu
SOURCE: csulb.edu
Establish a Contract Audit Trail
Working with digital contracts, ideally via a contract lifecycle management (CLM) solution, makes it easy to establish a detailed audit trail. With an audit trail you know what changes were made to a contract, when, and by whom. Auditors can review a contract’s audit trail during the contract compliance process to ensure that a contract that started in compliance remains in compliance. Any changes made during the compliance process can also be added to the audit trail.
Encrypt All Files and Communications
A contract compliance process is, in most instances, collaborative. Team members communicate with each other via emails, text messages, phone calls, and video meetings. These communications often contain confidential information, as do the files that team members share with one another.
Malicious actors can intercept these communications and shared files and gain access to your firm’s valuable contract data. This points out the need to secure all communications and collaborations, which is best done by using encryption.
Unfortunately, not all companies think to encrypt their employees’ communications. In fact, 24% of IT professionals surveyed say that unencrypted data is one of their top security vulnerabilities.
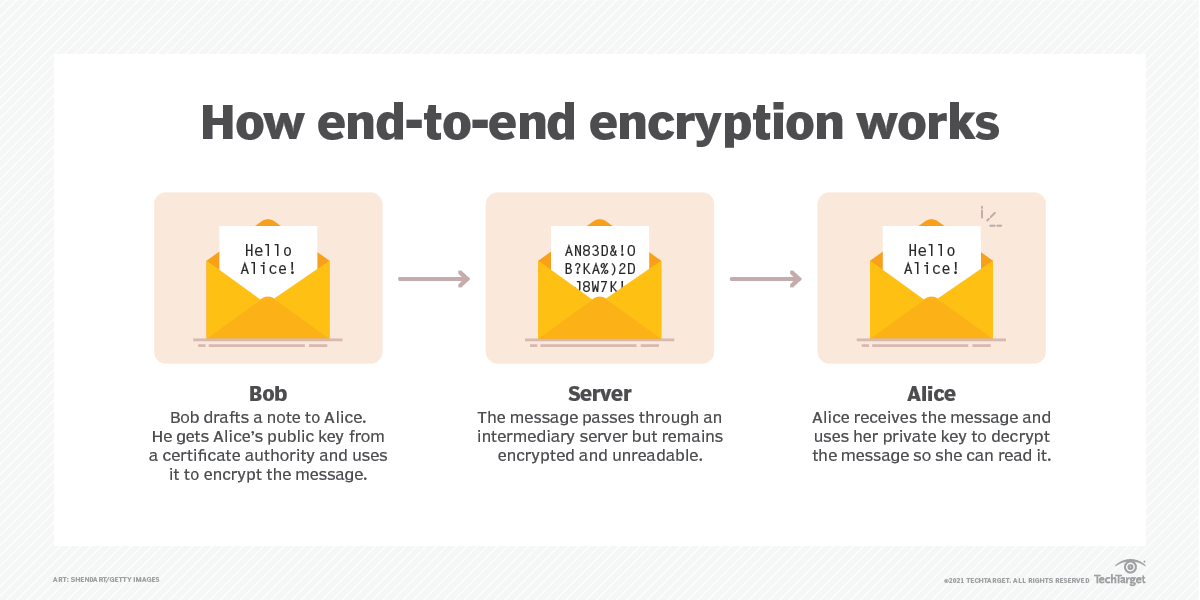
There are two types of encryption in use today. Encryption at-rest protects stored files (and should be used for your firm’s central contract repository), but to protect communications, you’ll need to employ encryption in-transit. This is typically done via the use of end-to-end encryption technology that encrypts a message at its source and keeps it encrypted until it’s received. Anyone hijacking an encrypted communication sees only gibberish.
 SOURCE: techtarget.com
SOURCE: techtarget.com
Deploy a CLM Solution
The easiest and most effective way to protect your valuable data during the contract compliance process is to embrace a contract lifecycle management solution. A comprehensive CLM solution, such as that from Contract Logix, includes all the security features mentioned here and a lot more. Organizations of all types and sizes use CLM software to speed up contract workflow, minimize errors, and reduce costs.
Turn to Contract Logix to Ensure Data Protection During the Contract Compliance Process
When you want to ensure that your data stays secure during the contract compliance process, turn to the experts at Contract Logix. Our CLM Platform not only automates the entire contract lifecycle, it provides robust contract security and a detailed audit trail. You’ll keep your contract data secure and realize other benefits, including streamlined workflow, improved accuracy, and lower costs.
Contact Contract Logix today to learn more about data protection and the contract compliance process.


