8 Ways to Implement CLM Security
According to Varonis’ Global Data Risk Report, only 5% of the folders in any organization are properly protected. This means that even if you’ve digitized your contract management and storage using a document storage platform such as Box, Dropbox, or SharePoint, your contracts are still at risk of breaches or attacks. To properly protect your organization’s valuable contract information, you must implement robust CLM security practices.
Following eight key steps can help you implement this added security without slowing down the contract management process.
Key Takeaways
- CLM security protects your contracts from loss, unauthorized access, or theft.
- Lax CLM security can result in unnecessary risks such as missed deadlines, leaked secrets, compromised customer/vendor privacy, hefty fines, and possible legal action.
- To implement CLM security, digitize all contracts and store them in a central cloud-based CLM repository secured by access control and encryption.
- CLM solutions such as Contract Logix ensure robust CLM security along with numerous other benefits.
What is CLM Security?
Contract management security encompasses all the systems and technologies used to protect contracts from unauthorized access, loss, or theft. The best contract security works in the background to protect your contracts without compromising efficiency and access to the valuable data stored in those contracts.
The goal of contract management security is to ensure that employees have access to those contracts necessary to perform their jobs while blocking access to everyone else both inside and outside the organization. It’s a matter of protecting against data breaches, data theft, ransomware, and other cyberattacks.
Many people think of contract management security as solely guarding against external threats from malicious actors. While that’s an important part of your security efforts, you also need to protect against internal threats from current or former employees. This can include clearly malicious behavior from disgruntled employees, more innocent “rogue contracts” executed without going through normal channels, or enabling employees to access data that they have no reason or right to access.
Contract management security must protect against all these threats, malicious or otherwise. Without appropriate security measures, your entire organization is at risk.
Why is Contract Management Security Important?
What risks can arise from ineffective or nonexistent contract management security? Here are just some of the more significant issues:
- Missing deadlines and deliverables due to misplaced, stolen, or deleted contracts
- Incurring fines or legal action resulting from unfulfilled contractual obligations
- Missing contract renewal dates
- Stolen company secrets and intellectual property ending up in the hands of competitors
- Clients poached due to stolen contract data
- Stolen customer or vendor data leading to privacy issues
- Noncompliance with privacy and other governmental and industry regulations, such as PCI, SOC 2 Type 2, HIPAA, and FISMA, and resulting fines or legal action
In addition, lax contract management security can lead to lost or misplaced contracts both post-execution and during the approval process. This can slow down the entire contract management process and lead to contracts not being executed in a timely fashion or at all.
How Do You Implement Contract Management Security?
The key to avoiding all of these potential issues is to implement strong contract management security. Here are eight important ways to do so.
1. Digitize All Contracts and Supporting Documents
The first step in implementing contract management security is to move from physical contracts to digital ones. Start all new contracts in digital format and begin the process of digitizing existing paper contracts. You should also digitize all supporting documents, including COIs, SOWs, and BAAs.
2. Centralize All Contracts in a Single Digital Repository
Lax contract security often results from decentralized contract processes and scattered contracts across an organization. Instead of letting individual departments or offices execute their own contracts, centralize the entire contract management process in one place and store all digital contracts and supporting documents in a single digital repository.
3. Secure the Contract Repository
Your digital contract repository should be fully secured to minimize the risk of data breaches. This includes proper user authentication capabilities such as employing strong passwords, multi-factor authentication (MFA), single sign-on (SSO), anti-malware tools, and more. (Employing MFA alone reduces the likelihood of account compromise by 99.9%.)
4. Employ Access Control
Not every employee should have unfettered access to your stored contracts. Access should be on a need-to-use basis with role-based and feature-based permissions. This enables authorized employees to read or write certain types of contracts while having no access to all others.
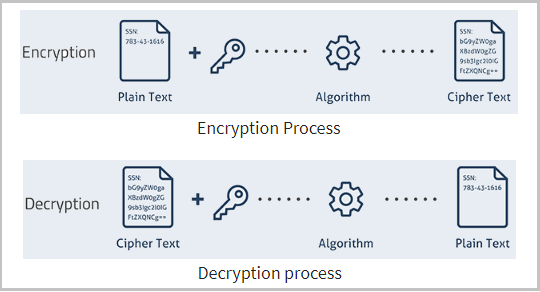
5. Encrypt All Contract Data
Further secure your stored contracts by encrypting all your digital files. In a recent survey, 24% of IT professionals say that unencrypted data is one of their company’s top security vulnerabilities. Encryption ensures that even if you experience a data breach, your contract data remains unreadable. Apply encryption to both data at rest using AES 256 (stored contracts) and data in transit via TLS 1.2 (contracts circulated for review and approvals).
SOURCE: Code-sample.com
6. Intake All New Data via Secure Forms
Malicious actors not only attack the data you’ve stored but also data before it has been secured. To prevent cybercriminals from accessing contract data while contracts are still being created, reviewed, and negotiated, you should require all parties to use secure digital forms to input all relevant data. Verify all data input to ensure it is accurate with nothing missing.
7. Embrace E-Signatures
Employing e-signatures for your contracts not only speeds up the approval and execution processes but also provides stronger security. Unlike physical signatures, e-signatures create a digital record of who signed the contracts, when, and where, providing secure authentication and an electronic audit trail. They also enable the signing of contracts from anywhere and any device which speeds up the process and improves the user experience.
(The following video shows how e-signatures work.)
SOURCE: Eye on Tech via YouTube
8. Deploy a CLM Solution
All of these approaches to contract management security are built into contract lifecycle management (CLM) platforms. Deploying a robust CLM solution, such as that offered by Contract Logix, provides all these CLM security features as well as speeding up the contract management process while reducing errors, risks and costs.
Turn to Contract Logix for CLM Security
When you want to employ robust contract management security, turn to the experts at Contract Logix. Our CLM Platform automates the entire contract lifecycle and centralizes the storage of all your contract data. You’ll also realize the benefits of streamlined workflow, improved accuracy, and lower costs, in addition to ensuring the security of your contract data.
Contact Contract Logix today to learn more about CLM security for your organization.


